Mobile Device Management Software Mac
- Mobile Device Management Software Vendors
- Mobile Device Management Software Mac Download
- Mobile Device Management Software For Mac
- Mobile Device Management Software Air
- Mobile Device Management Software Mac Pro
- Mobile Device Management For Ipad
- Mobile Device Management Software Comparison
Mar 18, 2020 Mobile device management is a crucial element of IT security. Then add in the near-ubiquity of cloud computing and software-as-a-service (SaaS). Along with Mac and Apple TV. Mobile device management (MDM) is an industry term for the administration of mobile devices, such as smartphones, tablet computers and laptops.MDM is usually implemented with the use of a third party product that has management features for particular vendors of mobile devices.
Simplify endpoint management in your organization with G Suite. Enforce passcodes and wipe specific accounts without installing software on a user's Android and iOS device with agentless endpoint management. This feature is on by default. Manage and secure. Mobile Device Management is a set of practices that involve enrolling, managing, monitoring, updating, securing and troubleshooting mobile devices such as smartphones, tablets, laptops, etc, in both LAN and WAN, from a central location. Enterprises today own and manage a diverse set of mobile.
Enroll your macOS device with the Intune Company Portal app to gain secure access to your work or school email, files, and apps.
Jun 07, 2018 To quit (close) a Mac app normally, choose Quit from the app's menu in the menu bar, or press Command (⌘)-Q. If the app doesn't quit, follow these steps to force the app to quit. How to force an app to quit. Press these three keys together: Option, Command, and Esc (Escape). This is similar to pressing Control-Alt-Delete on a PC. Sep 05, 2013 It does. But it still doesn't 'close' the app. Most document-based applications will remain open even with all windows closed. There's not really any problem with that, but most people coming from Windows do not understand that closing a window does not close the app. To minimize all windows of the front app, press Option-Command-M. Command-O: Open the selected item, or open a dialog to select a file to open. Command-P: Print the current document. Command-S: Save the current document. Command-T: Open a new tab. Command-W: Close the front window. To close all windows of the app, press Option-Command-W. Jul 02, 2014 Close All Windows in a Mac App with a Keystroke Jul 2, 2014 - 12 Comments Most Mac users know that hitting the Command+W keyboard shortcut will close the currently active window, but with a slight modification and by adding an additional key press, you can close all windows in just about any Mac OS X app or the Mac Finder. 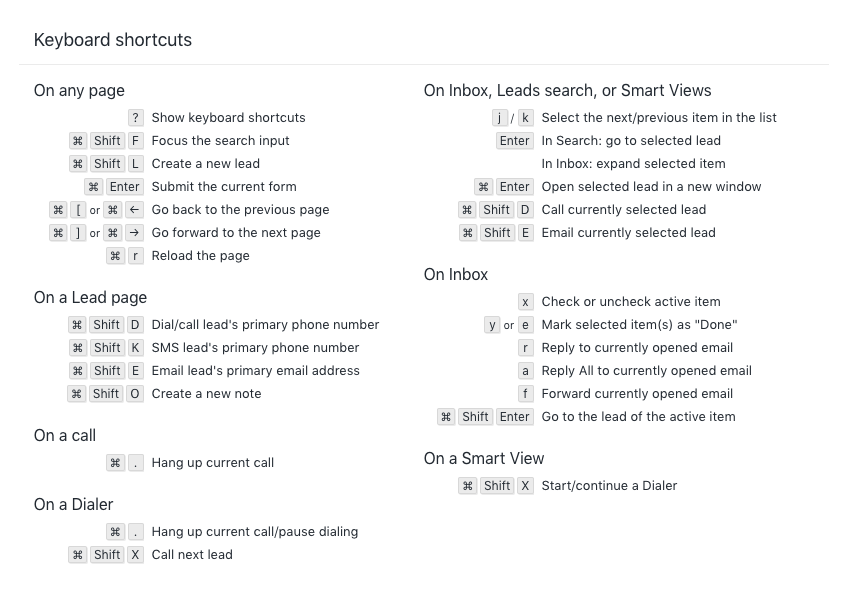
Organizations typically require you to enroll your device before you can access proprietary data. After your device is enrolled, it becomes managed. Your organization can assign policies and apps to the device through a mobile device management (MDM) provider, such as Intune. To get continuous access to work or school information on your device, you must set up your device to match your organization's policy settings.
This article describes how to use the Company Portal app for macOS to set up and maintain your device so that you meet your organization's requirements.
What to expect from the Company Portal app
During initial setup, the Company Portal app requires you to sign in and authenticate yourself with your organization. Company Portal then informs you of any device settings you need to configure to meet your organization's requirements. For example, organizations often set minimum or maximum character password requirements that you'll be required to meet.
After you enroll your device, Company Portal will always make sure that your device is protected according to your organization's requirements. For example, if you install an app from a source that's not trusted, Company Portal will alert you and might restrict access to your organization's resources. App protection policies like this one are common. To regain access, you'll likely need to uninstall the app.
If after enrollment your organization enforces a new security requirement, such as multi-factor authentication, Company Portal will notify you. You'll have the chance to adjust your settings so that you can continue to work from your device.
To learn more about enrollment, see What happens when I install the Company Portal app and enroll my device?.
Get your macOS device managed
Use the following steps to enroll your macOS device with your organization. Your device must be running macOS 10.12 or later.
Note
Throughout this process, you might be prompted to allow Company Portal to use confidential information that's stored in your keychain. These prompts are part of Apple security. When you get the prompt, type in your login keychain password and select Always Allow. If you press Enter or Return on your keyboard, the prompt will instead select Allow, which may result in additional prompts.
Install Company Portal app
- Go to Enroll My Mac.
- The Company Portal installer .pkg file will download. Open the installer and continue through the steps.
- Agree to the software license agreement.
- Enter your device password or registered fingerprint to install the software.
- Open Company Portal.
Important
Microsoft AutoUpdate might open to update your Microsoft software. After all updates are installed, open the Company Portal app. For the best setup experience, install the latest versions of Microsoft AutoUpdate and Company Portal.
Enroll your Mac
Sign in to Company Portal with your work or school account.
When the app opens, select Begin.
Review what your organization can and can't see on your enrolled device. Then select Continue.
On the Install management profile screen, select Download profile.
Your device's system preferences will open.
a. Select Install and then select Install again.
b. If you’re prompted to, enter your device password.Once the profile is installed, it will appear in the profiles list under Management Profile.
Return to Company Portal.
Your organization might require you to update your device settings. When you're done updating settings, select Retry.
When setup is complete, select Done.
Troubleshooting and feedback
If you run into issues during enrollment, go to Help > Send Diagnostic Report to report the issue to Microsoft app developers. This information is used to help improve the app. They'll also use this information to help resolve the problem if your IT support person reaches out to them for help.
After you report the problem to Microsoft, you can send the details of your experience to your IT support person. Select Email Details. Type in what you experienced in the body of the email. To find your support person's email address, go to the Company Portal app > Contact. Or check the Company Portal website.
Additionally, the Microsoft Intune Company Portal team would love to hear your feedback. Go to Help > Send Feedback to share your thoughts and ideas.
Unverified profiles
When you view the installed mobile device management (MDM) profiles in System Preferences > Profiles, some profiles might show an unverified status. As long as the management profile shows a verified status, you don't need to be concerned.
The management profile is what defines the MDM channel connection. As long as the management profile is verified, any other profiles delivered to the machine via that channel inherit the security traits of the management profile.
Things to do software mac. You can create as many lists as needed, and assign them all a color for easy recognition.
Updating the Company Portal app
Updating the Company Portal app is done the same way as any other Office app, through Microsoft AutoUpdate for macOS. Find out more about updating Microsoft apps for macOS.
Next Steps
Still need help? Contact your company support. For contact information, check the Company Portal website.
Mobile device management (MDM) is an industry term for the administration of mobile devices, such as smartphones, tablet computers and laptops. MDM is usually implemented with the use of a third party product that has management features for particular vendors of mobile devices.
Overview[edit]
Mobile Device Management Software Vendors
MDM is typically a deployment of a combination of on-device applications and configurations, corporate policies and certificates, and backend infrastructure, for the purpose of simplifying and enhancing the IT management of end user devices. In modern corporate IT environments, the sheer number and diversity of managed devices (and user behavior) has motivated MDM solutions that allow the management of devices and users in a consistent and scalable way. The overall role of MDM is to increase device supportability, security, and corporate functionality while maintaining some user flexibility.
Many organizations administer devices and applications using MDM products/services. MDM primarily deals with corporate data segregation, securing emails, securing corporate documents on devices, enforcing corporate policies, and integrating and managing mobile devices including laptops and handhelds of various categories. MDM implementations may be either on-premises or cloud-based.
Some of the core functions of MDM include:
- Ensuring that diverse user equipment is configured to a consistent standard / supported set of applications, functions, or corporate policies
- Updating equipment, applications, functions, or policies in a scalable manner
- Ensuring that users use applications in a consistent and supportable manner
- Ensuring that equipment performs consistently
- Monitoring and tracking equipment (e.g. location, status, ownership, activity)
- Being able to efficiently diagnose and troubleshoot equipment remotely
MDM functionality can include over-the-air distribution of applications, data and configuration settings for all types of mobile devices, including mobile phones, smartphones, tablet computers, ruggedized mobile computers, mobile printers, mobile POS devices, etc. Most recently laptops and desktops have been added to the list of systems supported as Mobile Device Management becomes more about basic device management and less about the mobile platform itself. MDM tools are leveraged for both company-owned and employee-owned (BYOD) devices across the enterprise or mobile devices owned by consumers.[1][2] Consumer Demand for BYOD is now requiring a greater effort for MDM and increased security for both the devices and the enterprise they connect to,[3] especially since employers and employees have different expectations concerning the types of restrictions that should be applied to mobile devices.[4]
By controlling and protecting the data and configuration settings of all mobile devices in a network, MDM can reduce support costs and business risks. The intent of MDM is to optimize the functionality and security of a mobile communications network while minimizing cost and downtime.[5]
With mobile devices becoming ubiquitous and applications flooding the market, mobile monitoring is growing in importance.[6] The use of mobile device management across continues to grow at a steady pace, and is likely to register a compound annual growth rate (CAGR) of nearly 23% through 2028. The US will continue to be the largest market for mobile device management globally.[7] Numerous vendors help mobile device manufacturers, content portals and developers test and monitor the delivery of their mobile content, applications and services. This testing of content is done in real time by simulating the actions of thousands of customers and detecting and correcting bugs in the applications.
Implementation[edit]
Typically solutions include a server component, which sends out the management commands to the mobile devices, and a client component, which runs on the managed device and receives and implements the management commands. In some cases, a single vendor provides both the client and the server, while in other cases the client and server come from different sources.
The management of mobile devices has evolved over time. At first it was necessary to either connect to the handset or install a SIM in order to make changes and updates; scalability was a problem.
One of the next steps was to allow a client-initiated update, similar to when a user requests a Windows Update.
Central remote management, using commands sent over the air, is the next step. An administrator at the mobile operator, an enterprise IT data center or a handset OEM can use an administrative console to update or configure any one handset, group or groups of handsets. This provides scalability benefits particularly useful when the fleet of managed devices is large in size.
Device management software platforms ensure that end-users benefit from plug and play data services for whatever device they are using.[citation needed] Such a platform can automatically detect devices in the network, sending them settings for immediate and continued usability. The process is fully automated, keeps a history of used devices and sends settings only to subscriber devices which were not previously set, sometimes at speeds reaching 50 over-the-air settings update files per second.[citation needed] Device management systems can deliver this function by filtering IMEI/IMSI pairs.[citation needed]
Device management specifications[edit]
- The Open Mobile Alliance (OMA) specified a platform-independent device management protocol called OMA Device Management. The specification meets the common definitions of an open standard, meaning the specification is freely available and implementable. It is supported by several mobile devices, such as PDAs and mobile phones.[8]
- Smart message is text SMS-based provisioning protocol (ringtones, calendar entries but service settings also supported like: ftp, telnet, SMSC number, email settings, etc..)
- OMA Client Provisioning is a binary SMS-based service settings provisioning protocol.
- Nokia-Ericsson OTA is binary SMS-based service settings provisioning protocol, designed mainly for older Nokia and Ericsson mobile phones.
Over-the-air programming (OTA) capabilities are considered a main component of mobile network operator and enterprise-grade mobile device management software. These include the ability to remotely configure a single mobile device, an entire fleet of mobile devices or any IT-defined set of mobile devices; send software and OS updates; remotely lock and wipe a device, which protects the data stored on the device when it is lost or stolen; and remote troubleshooting. OTA commands are sent as a binary SMS message. Binary SMS is a message including binary data.[9]
Mobile device management software enables corporate IT departments to manage the many mobile devices used across the enterprise; consequently, over-the-air capabilities are in high demand. Enterprises using OTA SMS as part of their MDM infrastructure demand high quality in the sending of OTA messages, which imposes on SMS gateway providers a requirement to offer a high level of quality and reliability.
Use in enterprise[edit]

As the bring your own device (BYOD) approach becomes increasingly popular across mobile service providers, MDM lets corporations provide employees with access to the internal networks using a device of their choice, whilst these devices are managed remotely with minimal disruption to employees' schedules.
For mobile security[edit]
All MDM products are built with an idea of Containerization. The MDM Container is secured using the latest cryptographic techniques (AES-256 or more preferred[citation needed]). Corporate data such as email, documents, and enterprise applications are encrypted and processed inside the container. This ensures that corporate data is separated from user's personal data on the device. Additionally, encryption for the entire device and/or SD Card can be enforced depending on MDM product capability.
Secure email: MDM products allow organizations to integrate their existing email setup to be easily integrated with the MDM environment. Almost all MDM products support easy integration with Exchange Server (2003/2007/2010), Office365, Lotus Notes, BlackBerry Enterprise Server (BES) and others. This provides the flexibility of configuring email over the air.
Secure docs: Employees frequently copy attachments downloaded from corporate email to their personal devices and then misuse it. MDM can restrict or disable clipboard usage into or out of the secure container, restrict forwarding of attachments to external domains, or prevent saving attachments on SD card. This ensures corporate data is secure.
Secure browser: Using a secure browser can avoid many potential security risks. Every MDM solution comes with built-in custom browser. An administrator can disable native browsers to force users to use the secure browser inside the MDM container. URL filtering can be enforced to add additional security measures.
Secure app catalog: Organizations can distribute, manage, and upgrade applications on an employee's device using an App Catalogue. This allows applications to be pushed onto the user's device directly from the App Store or push an enterprise developed private application through the App Catalogue. This provides an option for the organization to deploy devices in Kiosk Mode or Lock-Down Mode.
Additional MDM features[edit]
Mobile Device Management Software Mac Download
There are plenty of other features depending on which MDM product is chosen:
Mobile Device Management Software For Mac
- Policy Enforcing: There are multiple types of policies which can be enforced on MDM users.
- Personal Policy: According to corporate environment, highly customizable
- Device Platform specific: policies for advanced management of Android, iOS, Windows and Blackberry devices.
- Compliance Policies/Rules
- VPN configuration
- Application Catalogue
- Pre-defined Wi-Fi and Hotspot settings
- Jailbreak/Root detection
- Remote Wipe of corporate data
- Remote Wipe of entire device
- Device remote locking
- Remote messaging/buzz
- Disabling native apps on device
- Some Kiosk software features[10]
SaaS versus on-premises solutions[edit]
Mobile Device Management Software Air
Present day MDM solutions offer both software as a service (SaaS) and on-premises models. In the rapidly evolving industry such as mobile, SaaS (cloud-based) systems are sometimes quicker to set up, offer easier updates with lower capital costs compared to on-premises solutions which require hardware or virtual machines, need regular software maintenance, and might incur higher capital costs.
For security in cloud computing, the US Government has compliance audits such as Federal Information Security Management Act of 2002 (FISMA) which cloud providers can go through to meet security standards.
The primary policy approach taken by Federal agencies to build relationships with cloud service providers is Federal Risk and Authorization Management Program (FedRAMP) accreditation and certification, designed in part to protect FISMA Low, Moderate, High and Li-SaaS systems.[11]
Evolution of MDM[edit]
MDM is also about managing the device features, but its coupled with mobile content management (MCM) and Mobile Identity Management (MIM), Application management (MAM) it called as Enterprise Mobility Management (EMM). As EMM was specifically about managing the apps and content on mobile devices it was not able to manage older devices such as Windows laptops/desktops and new Macs, so EMM evolved into UEM (Unified Endpoint Management) with additional functionality to manage both mobile and traditional devices such as desktops and laptops.
See also[edit]
References[edit]
Mobile Device Management Software Mac Pro
- ^What is mobile device management? - a definition from Whatis.com
- ^'A comprehensive article on mobile device management'. Archived from the original on 2012-08-01. Retrieved 2008-02-04.
- ^Glenn Ford. 'Cybersecurity HQ'. Retrieved 19 December 2014.
- ^Ellis, Lisa, Jeffrey Saret, and Peter Weed (2012). 'BYOD: From company-issued to employee-owned devices'(PDF). Telecom, Media & High Tech Extranet: No. 20 Recall. Retrieved 15 May 2014.CS1 maint: multiple names: authors list (link)
- ^'BYOD Requires Mobile Device Management'. Information Week.
- ^'A Playbook for Fighting Apple and Google'. Reuters. 15 March 2011.
- ^'Japan to Hold Notable Market Potential in Mobile Device Management Landscape'. Abhishek Budholiya. 5 December 2018.
- ^'What Is OMA DM?'(PDF).
- ^'Binary SMS'. Archived from the original on 2016-08-01. Retrieved 19 December 2014.
- ^'Mobile Device Management vs. Kiosk Software' in Kiosk Marketplace
- ^'FedRAMP - CIO Council'. CIO Council. Retrieved 19 December 2014.